CrowdStrike Integration Guide
CrowdStrike is a cybersecurity provider. It provides cloud workload and endpoint security, threat intelligence, and cyberattack response services. TaskCall's CrowdStrike integration enhances incident response by transporting details of the security breaches to the on-call IT team through email, push notifications, SMS, voice calls and chat-ops integrations immediately after they are detected by CrowdStrike
Pointers
- The integration is between a TaskCall service and CrowdStrike.
- This integration allows details of security breach detections made by CrowdStrike to be directed to TaskCall.
- TaskCall automatically resolves the incidents when their corresponding alerts are "closed" or "ignored" in CrowdStrike.
In TaskCall
- Go to Configurations > Services . Select the service you want to integrate with.
- Once you are on the Service details page, go to the Integrations tab. Click on New Integration.
- Give the integration a name.
- From the integration types, select the top radio button indicating that you are trying to use a built-in integration.
- From the list of built-in integrations, select CrowdStrike.
- Click Save.
- Copy the Integration Url that is issued for the integration.
In CrowdStrike
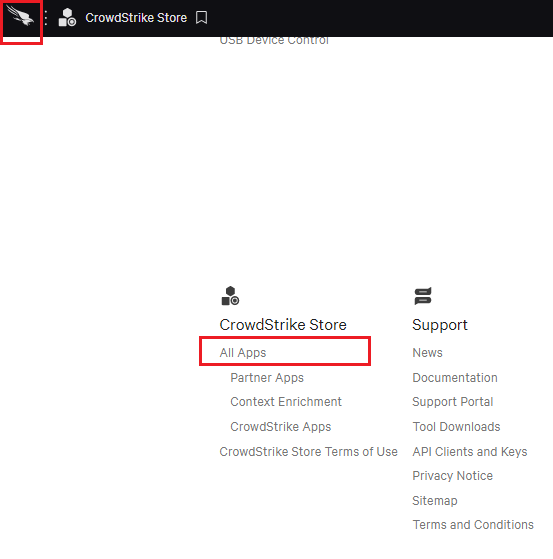
- Click the CrowdStrike icon on the top right corner to navigate to the menu selection. Scroll down to the CrowdStrike Store. Click All Apps.
- Scroll down to the Plugins section and select Webhook.
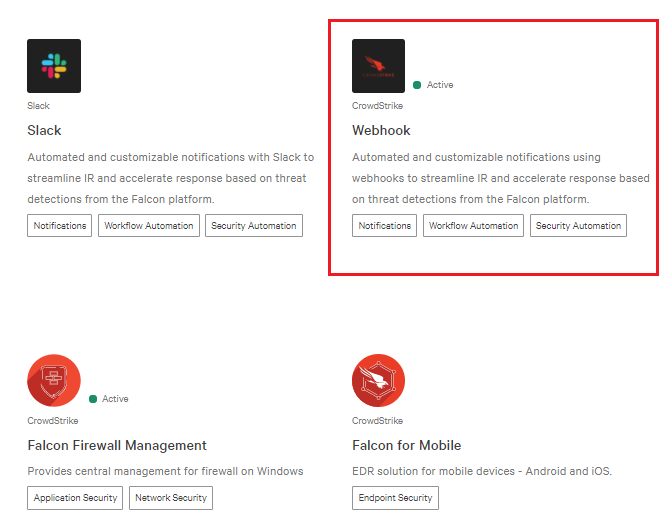
- Click Configure and then Add configuration.
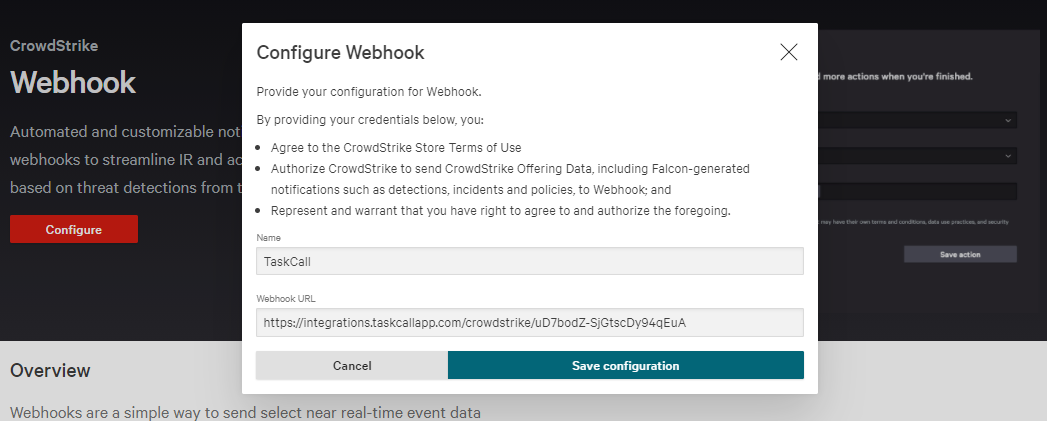
- Name the webhook TaskCall and paste the Integration Url you copied over from TaskCall in the Webhook URL field. Click Save configuration .
- Go back to the menu selection and select Notification Workflows.
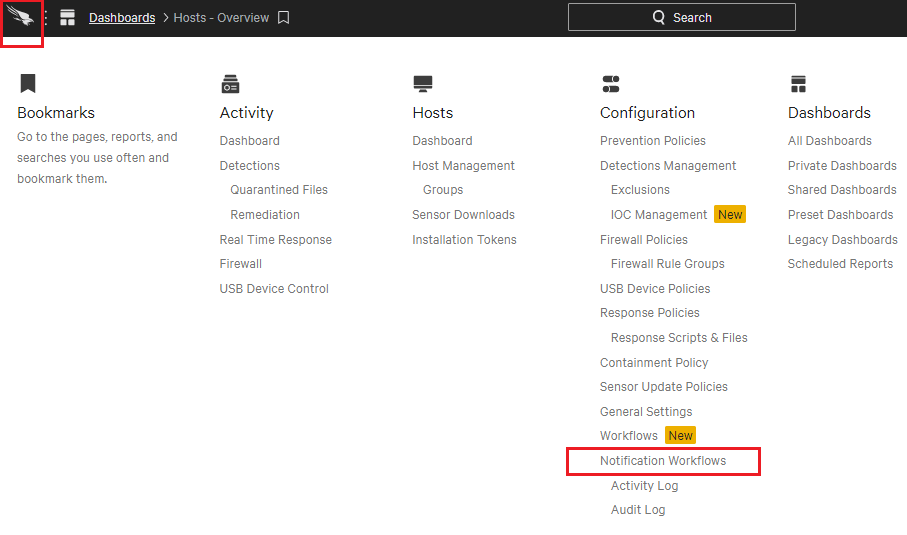
- Click Create a workflow.
- Select the Detections workflow category and click Next.
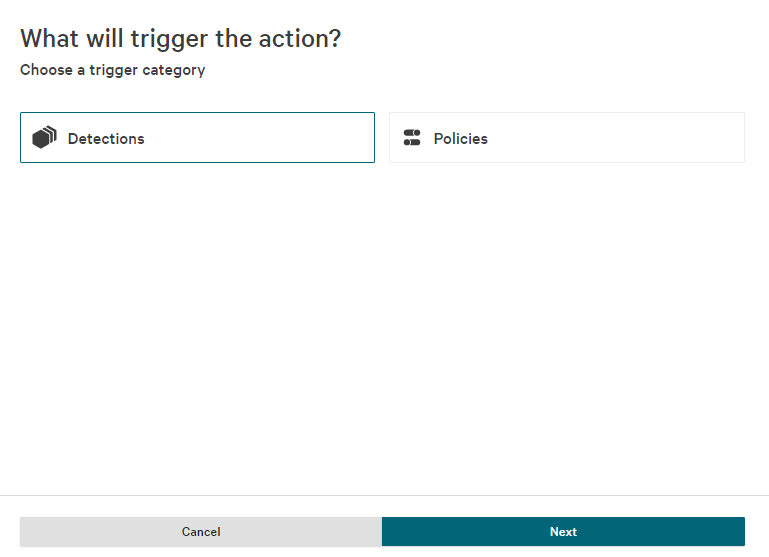
- Select New detection and hit Next.
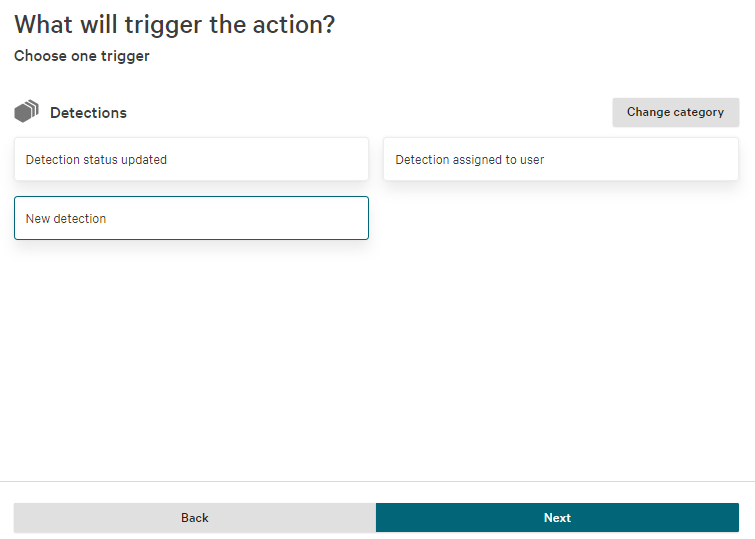
- Set up the conditions that you want the webhook to be called on.
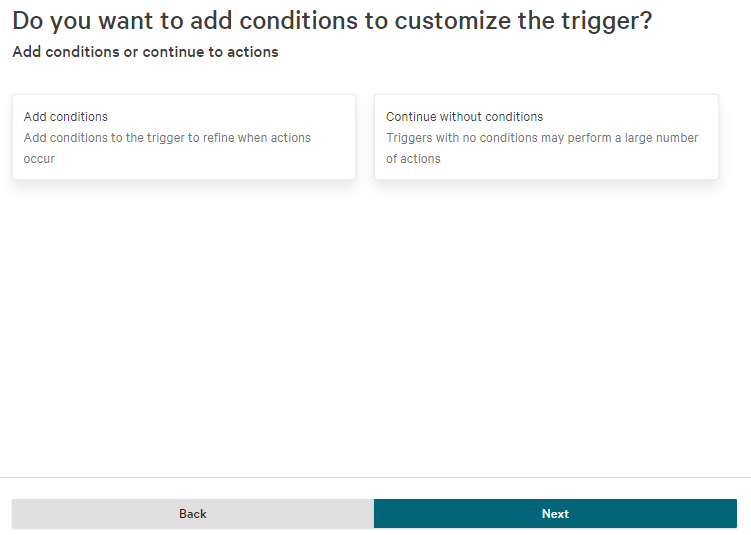
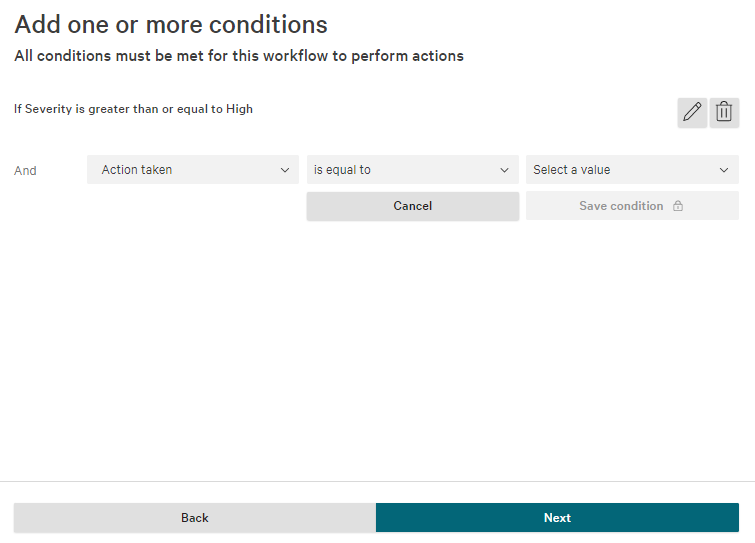
- When you move on to the Actions page, select Call webhook as the action. Select the TaskCall webhook you created earlier. Then select the following data fields in the Data to include section:
- Action taken
- Cloud service instance ID
- Cloud service provider
- Cloud service provider account ID
- Detection URL
- Domain
- External IP address
- Hostname
- Host type
- IOC type
- IOC value
- Objective
- Severity
- Site
- Tags
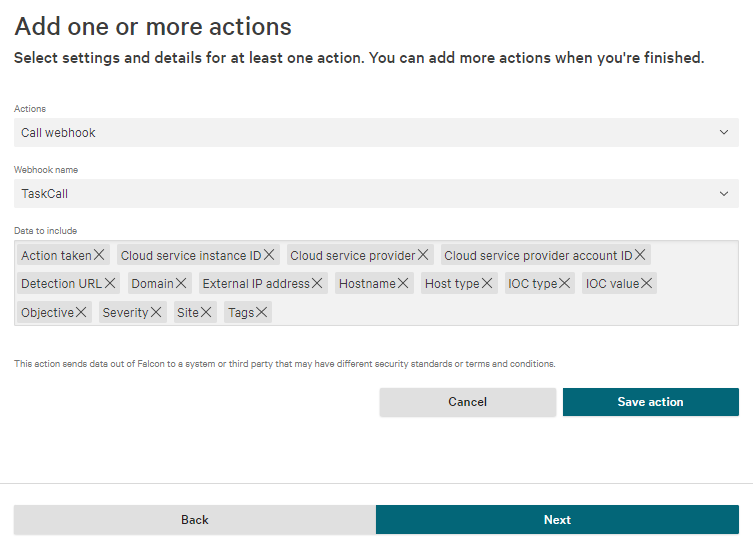
- Click Save action. Click Next.
- Give the workflow a name and a description.
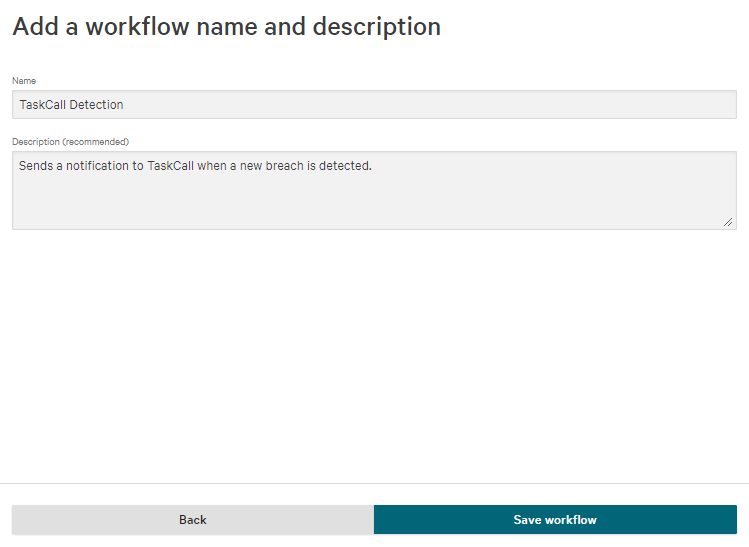
- Click Save workflow.
- Great! We have set up the workflow to trigger incidents on TaskCall when a new incident is detected. Now we will set up two more workflows to resolve the incidents when they are "closed" and "ignored" in CrowdStrike respectively.
- Repeat the exact same process as above, but in the step where you set the conditions you should select Status is equal to Closed .
- And in the actions segment, this time select the following data fields in the Data to include section:
- Detection ID
- Modified by
- Status
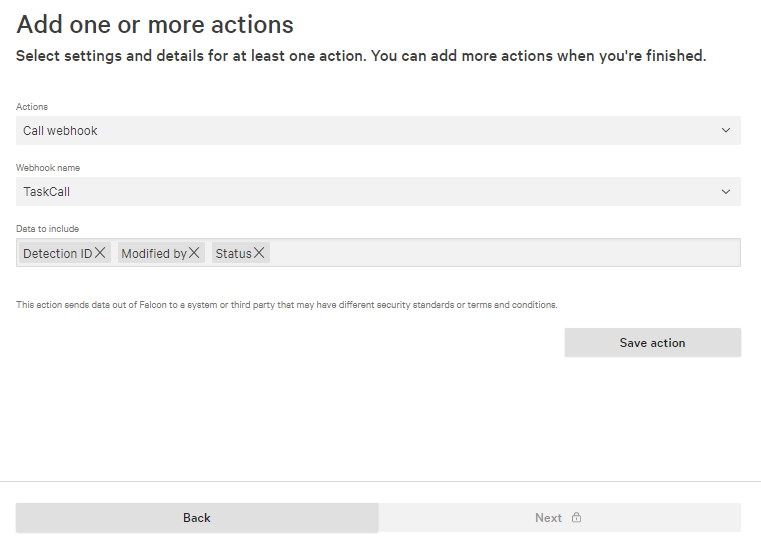
- Repeat the last two steps to set up a webhook trigger when the Status is equal to Ignored as well.
- Done!
Please make sure that you follow the instructions above correctly and create 3 different notification workflows. The first one to trigger when a new breach is detected, the second for when the alert is closed and the third one for when the alert is ignored.