Splunk Integration Guide
Splunk provides a powerful platform for searching, monitoring and analyzing machine generated data. It allows organizations prevent major issues and stay resilient when problems manifest. It can be configured to identify errors periodically or in real time through logs or user device activity. TaskCall integrates with Splunk to bring the alerts to the forefront. As alerts are piped by Splunk, TaskCall’s on-call management directs them to the correct on-call responder and our incident response system orchestrates the fastest possible resolution.
Pointers
- The integration is between a TaskCall service and Splunk.
- This integration only allows alerts to be received in TaskCall from Splunk.
In TaskCall
- Go to Configurations > Services . Select the service you want to integrate with.
- Once you are on the Service details page, go to the Integrations tab. Click on New Integration.
- Give the integration a name.
- From the integration types, select the top radio button indicating that you are trying to use a built-in integration.
- From the list of built-in integrations, select Splunk.
- Click Save.
- Copy the Integration Url that is issued for the integration.
In Splunk
- Alerts in Splunk are configured from saved searches. Render the search you want to set up the alert from. Click on the Save As dropdown on the top right corner of the search results page and then click Alert.
- Configure the alert. Give it a name, describe it and set the schedule when the alert should run.
- In the Trigger Actions section at the bottom, click Add Actions and select Webhook. Paste the integration URL that you copied over from TaskCall here.
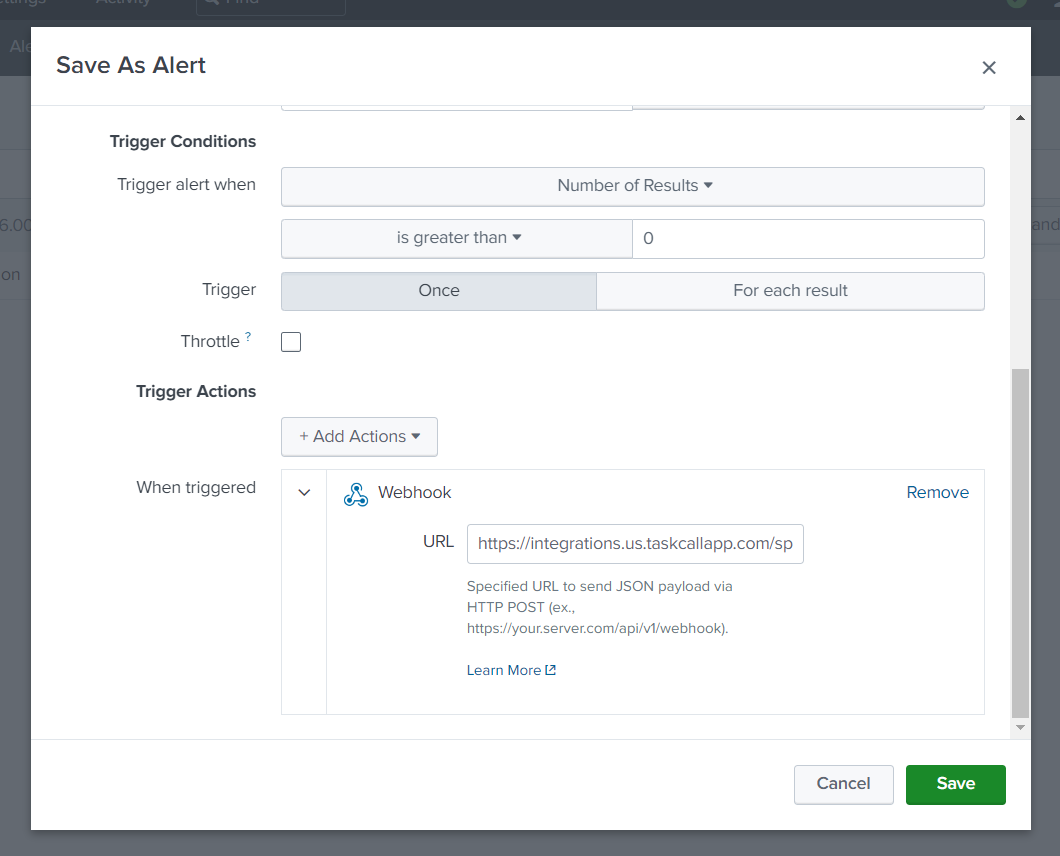
- Click Save when you are done.
You can repeat the same steps for other alerts to pipe them to TaskCall.